SITE-A-router(config)#interface serial 4/0
SITE-A-router(config-if)#ip address 1.1.1.1 255.0.0.0
SITE-A-router(config-if)#no shutdown
SITE-A-router(config-if)#exit
SITE-A-router(config)#interface fastethernet 0/0
SITE-A-router(config-if)#ip address 10.1.1.1 255.0.0.0
SITE-A-router(config-if)#no shutdown
SITE-A-router(config-if)#exit
R2(config)#interface serial 4/0
R2(config-if)#ip address 1.1.1.2 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface serial 4/1
R2(config-if)#ip address 3.3.3.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface serial 4/2
R2(config-if)#ip address 4.4.4.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#exit
SITE-B-router(config)#interface serial 4/1
SITE-B-router(config-if)#ip address 3.3.3.2 255.0.0.0
SITE-B-router(config-if)#no shutdown
SITE-B-router(config-if)#exit
SITE-B-router(config)#interface fastethernet 0/0
SITE-B-router(config-if)#ip address 30.1.1.1 255.0.0.0
SITE-B-router(config-if)#no keepalive
SITE-B-router(config-if)#no shutdown
SITE-B-router(config-if)#exit
SITE-C-router(config)#interface serial 4/2
SITE-C-router(config-if)#ip address 4.4.4.2 255.0.0.0
SITE-C-router(config-if)#no shutdown
SITE-C-router(config-if)#exit
SITE-C-router(config)#interface fastethernet 0/0
SITE-C-router(config-if)#ip address 40.1.1.1 255.0.0.0
SITE-C-router(config-if)#no keepalive
SITE-C-router(config-if)#no shutdown
SITE-C-router(config-if)#exit
- Configure default route at Site-A, Site-B and Site-C
SITE-A-router(config)#ip route 0.0.0.0 0.0.0.0 serial 4/0
SITE-B-router(config)#ip route 0.0.0.0 0.0.0.0 serial 4/1
SITE-C-router(config)#ip route 0.0.0.0 0.0.0.0 serial 4/2
- Configure static routing on router 2 which is acting as an internet router
internet(config)#ip route 10.0.0.0 255.0.0.0 serial 4/0
internet(config)#ip route 30.0.0.0 255.0.0.0 serial 4/1
internet(config)#ip route 40.0.0.0 255.0.0.0 serial 4/2
SITE-A-router#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/0
SITE-B-router#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/1
SITE-C-router#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/2
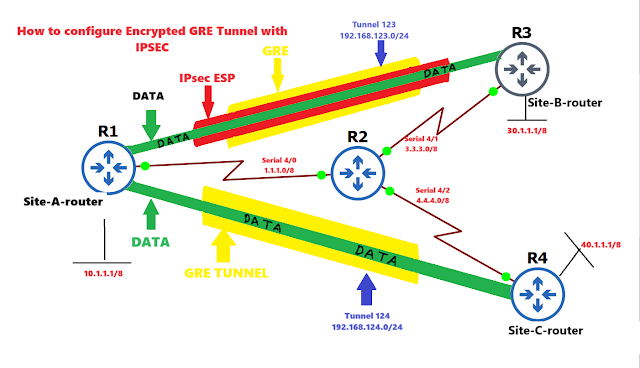
- Configure the GRE tunnel between Site-A to Site-B, the IP address of the tunnel will be 192.168.123.0/24
SITE-A-router(config)#interface tunnel 123
SITE-A-router(config-if)#ip address 192.168.123.1 255.255.255.0
SITE-A-router(config-if)#ip mtu 1400
SITE-A-router(config-if)#ip tcp adjust-mss 1360
SITE-A-router(config-if)#tunnel source 1.1.1.1
SITE-A-router(config-if)#tunnel destination 3.3.3.2
SITE-A-router(config-if)#exit
*Jan 5 14:54:33.579: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel124,changed state to up
SITE-B-router(config)#interface tunnel 123
SITE-B-router(config-if)#ip address 192.168.123.2 255.255.255.0
SITE-B-router(config-if)#ip mtu 1400
SITE-B-router(config-if)#ip tcp adjust-mss 1360
SITE-B-router(config-if)#tunnel source 3.3.3.2
SITE-B-router(config-if)#tunnel destination 1.1.1.1
SITE-B-router(config-if)#exit
*Jan 5 14:44:06.719: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel123,changed state to up
SITE-A-router#show ip interface brief | ex unass
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.1.1 YES manual down up
Serial4/0 1.1.1.1 YES manual up up
Tunnel123 192.168.123.1 YES manual up up
- Configure EIGRP on Site-A and Site-B and advertise LAN network and tunnel IP
SITE-A-router(config)#router eigrp 123
SITE-A-router(config-router)#network 10.0.0.0
SITE-A-router(config-router)#network 192.168.123.0
SITE-A-router(config-router)#no auto-summary
SITE-A-router(config-router)#exit
*Jan 5 14:45:42.327: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 123: Neighbor 192.168.123.2 (Tunnel123) is up: new adjacency
*Jan 5 14:45:54.175: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 123: Neighbor 192.168.123.2 (Tunnel123) is resync: peer graceful-restart
SITE-B-router(config)#router eigrp 123
SITE-B-router(config-router)#network 30.0.0.0
SITE-B-router(config-router)#network 192.168.123.0
SITE-B-router(config-router)#no auto-summary
SITE-B-router(config-router)#exit
*Jan 5 14:45:53.559: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 123: Neighbor 192.168.123.1(Tunnel123) is resync: summary configured
*Jan 5 14:45:41.811: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 123: Neighbor 192.168.123.1 (Tunnel123) is up: new adjacency
SITE-A-router#ping 30.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 48/60/64 ms
- Verify the tunnel with show commands and trace commands to make sure data will travel in the tunnel created.
SITE-A-router#traceroute 30.1.1.1
Type escape sequence to abort.
Tracing the route to 30.1.1.1
1 192.168.123.2 56 msec 64 msec 56 msec
SITE-A-router#traceroute 40.1.1.1
Type escape sequence to abort.
Tracing the route to 40.1.1.1
1 1.1.1.2 52 msec 32 msec 36 msec
2 4.4.4.2 56 msec 64 msec 68 msec
Same way configure the GRE tunnel for Site-C and remember we encrypt the entire tunnel only for Site-A to Site-B not for Site-C.
SITE-A-router(config)#interface tunnel 124
SITE-A-router(config-if)#ip address 192.168.124.1 255.255.255.0
SITE-A-router(config-if)#ip mtu 1400
SITE-A-router(config-if)#ip tcp adjust-mss 1360
SITE-A-router(config-if)#tunnel source 1.1.1.1
SITE-A-router(config-if)#tunnel destination 4.4.4.2
SITE-A-router(config-if)#exit
*Jan 5 19:52:36.575: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel124, changed state to up
SITE-C-router(config)#interface tunnel 124
SITE-C-router(config-if)#ip address 192.168.124.2 255.255.255.0
SITE-C-router(config-if)#ip mtu 1400
SITE-C-router(config-if)#ip tcp adjust-mss 1360
SITE-C-router(config-if)#tunnel source 4.4.4.2
SITE-C-router(config-if)#tunnel destination
SITE-C-router(config-if)#tunnel destination 1.1.1.1
SITE-C-router(config-if)#exit
*Jan 5 19:53:48.111: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel124, changed state to up
SITE-A-router(config)#router eigrp 123
SITE-A-router(config-router)#network 192.168.124.0
SITE-A-router(config-router)#exit
SITE-C-router(config)#router eigrp 123
SITE-C-router(config-router)#network 192.168.124.0
SITE-C-router(config-router)#network 40.0.0.0
SITE-C-router(config-router)#no auto-summary
SITE-C-router(config-router)#exit
SITE-A-router#show ip interface brief | exclude unass
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.1.1 YES manual up up
Serial4/0 1.1.1.1 YES manual up up
Tunnel123 192.168.123.1 YES manual up up
Tunnel124 192.168.124.1 YES manual up up
SITE-A-router#traceroute 40.1.1.1
Type escape sequence to abort.
Tracing the route to 40.1.1.1
1 192.168.124.2 72 msec 48 msec 56 msec
SITE-A-router#traceroute 30.1.1.1
Type escape sequence to abort.
Tracing the route to 30.1.1.1
1 192.168.123.2 52 msec 56 msec 64 msec
- After establishing the GRE tunnel, Configure the IPsec tunnel
SITE-A-router(config)#crypto isakmp policy 123
SITE-A-router(config-isakmp)#authentication pre-share
SITE-A-router(config-isakmp)#hash sha
SITE-A-router(config-isakmp)#group 5
SITE-A-router(config-isakmp)#encryption aes
SITE-A-router(config-isakmp)#exit
SITE-B-router(config)#crypto isakmp policy 123
SITE-B-router(config-isakmp)#authentication pre-share
SITE-B-router(config-isakmp)#hash sha
SITE-B-router(config-isakmp)#group 5
SITE-B-router(config-isakmp)#encryption aes
SITE-B-router(config-isakmp)#exit
SITE-A-router(config)#crypto isakmp key 0 internetworks address 3.3.3.2
SITE-B-router(config)#crypto isakmp key 0 internetworks address 1.1.1.1
SITE-A-router(config)#crypto ipsec transform-set GRE-TRANS esp-aes esp-sha-hmac
SITE-A-router(cfg-crypto-trans)#exit
SITE-B-router(config)#crypto ipsec transform-set GRE-TRANS esp-aes esp-sha-hmac
SITE-B-router(cfg-crypto-trans)#exit
SITE-A-router(config)#crypto ipsec profile GRE-PROF
SITE-A-router(ipsec-profile)#set transform-set GRE-TRANS
SITE-A-router(ipsec-profile)#exit
SITE-B-router(config)#crypto ipsec profile GRE-PROF
SITE-B-router(ipsec-profile)#set transform-set GRE-TRANS
SITE-B-router(ipsec-profile)#exit
apply the tunnel protection IPsec profile on the tunnel interface
SITE-A-router(config)#interface tunnel 123
SITE-A-router(config-if)#tunnel protection ipsec profile GRE-PROF
SITE-A-router(config-if)#exit
*Jan 5 20:24:26.299: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
SITE-B-router(config)#interface tunnel 123
SITE-B-router(config-if)#tunnel protection ipsec profile GRE-PROF
SITE-B-router(config-if)#exit
*Jan 5 20:25:15.783: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
*Jan 5 20:25:16.739: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1234: Neighbor 192.168.123.2 (Tunnel123) is up: new adjacency
*Jan 5 20:25:17.067: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1234: Neighbor 192.168.123.1 (Tunnel123) is up: new adjacency
SITE-A-router#ping 30.1.1.1 source 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/56/68 ms
- Make sure the entire tunnel will encrypt data.
SITE-A-router#show crypto ipsec sa
interface: Tunnel123
Crypto map tag: Tunnel123-head-0, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (3.3.3.2/255.255.255.255/47/0)
current_peer 3.3.3.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 33, #pkts encrypt: 33, #pkts digest: 33
#pkts decaps: 32, #pkts decrypt: 32, #pkts verify: 32
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 11, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 3.3.3.2
path mtu 1500, ip mtu 1500, ip mtu idb Serial4/0
current outbound spi: 0xFCE55818(4242888728)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x190E17F4(420354036)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000046, crypto map: Tunnel123-head-0
sa timing: remaining key lifetime (k/sec): (4557035/3501)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xFCE55818(4242888728)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000046, crypto map: Tunnel123-head-0
sa timing: remaining key lifetime (k/sec): (4557034/3501)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
SITE-A-router#traceroute 30.1.1.1 source 10.1.1.1
Type escape sequence to abort.
Tracing the route to 30.1.1.1
1 192.168.123.2 56 msec 56 msec 64 msec
SITE-B-router#ping 10.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 30.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 48/66/84 ms
SITE-B-router#show crypto ipsec sa
interface: Tunnel123
Crypto map tag: Tunnel123-head-0, local addr 3.3.3.2
protected vrf: (none)
local ident (addr/mask/prot/port): (3.3.3.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
current_peer 1.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 67, #pkts encrypt: 67, #pkts digest: 67
#pkts decaps: 68, #pkts decrypt: 68, #pkts verify: 68
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 3.3.3.2, remote crypto endpt.: 1.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb Serial4/1
current outbound spi: 0x190E17F4(420354036)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xFCE55818(4242888728)














0 comments:
Post a Comment