DMVPN (Dynamic Multipoint VPN) Introduced by Cisco in late
2000 is a routing technology you can use to build a VPN network with
multiple sites (spokes) without having to statically configure all devices.
It’s a “hub and spoke” network, where the spokes will, can communicate with
each other directly without having to go through the hub. Encryption is
supported through IPsec which makes DMVPN a popular choice for connecting
different sites using regular Internet connections. It’s a great backup or
alternative to private networks like MPLS VPN.
As we already discussed Phase 1 is Not used nowadays, in phase 1 uses
NHRP so that spokes can register themselves with the hub (NHRP is needed for
spokes to register with the hub). The hub is the only router that is using a
multipoint GRE (mGRE) interface, all spokes will be using regular
point-to-point GRE tunnel interfaces. No spokes hub and spokes topology where dynamic IP addresses on the spokes may be used. All your traffic goes
through the hub. This means that there will be no direct
spoke-to-spoke communication; all traffic has to go through the hub.
So, our traffic has to go through the hub, and our routing
configuration will be quite simple. Spoke routers only need a summary or
default route to the hub to reach other spoke routers.
In DMVPN Phase 2 hub and spokes are configured as multipoint GRE and spoke-to-spokes tunnels are created, NHRP is required for spokes to register to Hub, and NHRP is also required for spoke-to-spoke resolution.
let's see the configuration: -
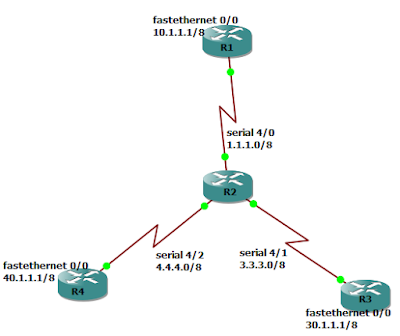
Topology: -
Goal:
- configure the topology as per the diagram
- assign the IP addresses to their port as per the
topology
- configure static routing on router 2
- configure default routing on router 1 3 4
- configure DMVPN Phase 2 on routers 1, 3 and 4
- configure router 1 Hub and router 3 and 4 should be
spokes routers
- configure tunnel interfaces 192.168.10.0/24
- configure NHRP using Stating mapping.
R1(config)#interface serial 4/0
R1(config-if)#ip address 1.1.1.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#ip address 10.1.1.1 255.0.0.0
R1(config-if)#no shutdown
R1(config-if)#no keepalive
R1(config-if)#exit
R2(config)#interface serial 4/0
R2(config-if)#ip address 1.1.1.2 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#interface serial 4/1
R2(config-if)#ip address 3.3.3.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#interface serial 4/2
R2(config-if)#ip address 4.4.4.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#interface fastethernet 0/0
R2(config-if)#ip address 20.1.1.1 255.0.0.0
R2(config-if)#no shutdown
R2(config-if)#no keepalive
R2(config-if)#exit
R3(config)#interface serial 4/1
R3(config-if)#ip address 3.3.3.2 255.0.0.0
R3(config-if)#no shutdown
R3(config-if)#interface fastethernet 0/0
R3(config-if)#ip address 30.1.1.1 255.0.0.0
R3(config-if)#no shutdown
R3(config-if)#no keepalive
R3(config-if)#exit
R4(config)#interface serial 4/2
R4(config-if)#ip address 4.4.4.2 255.0.0.0
R4(config-if)#no shutdown
R4(config-if)#interface fastethernet 0/0
R4(config-if)#ip address 40.1.1.1 255.0.0.0
R4(config-if)#no shutdown
R4(config-if)#no keepalive
R4(config-if)#exit
R1#show ip interface brief
Interface
IP-Address OK? Method Status
Protocol
FastEthernet0/0 10.1.1.1
YES manual up
up
Serial4/0
1.1.1.1 YES manual
up up
R2#show ip interface brief
Interface
IP-Address OK? Method Status
Protocol
FastEthernet0/0 20.1.1.1
YES manual up
up
Serial4/0
1.1.1.2 YES manual up
up
Serial4/1
3.3.3.1 YES manual up
up
Serial4/2
4.4.4.1 YES manual up
up
R3#show ip interface brief
Interface
IP-Address OK? Method Status
Protocol
FastEthernet0/0 30.1.1.1
YES manual up
up
Serial4/1
3.3.3.2 YES manual
up up
R4#show ip interface brief
Interface
IP-Address OK? Method Status
Protocol
FastEthernet0/0 40.1.1.1
YES manual up
up
Serial4/2
4.4.4.2 YES manual
up up
R1(config)#ip route 0.0.0.0 0.0.0.0 serial 4/0
R1(config)#exit
R2(config)#ip route 1.0.0.0 255.0.0.0 serial 4/0
R2(config)#ip route 10.0.0.0 255.0.0.0 serial 4/0
R2(config)#ip route 30.0.0.0 255.0.0.0 serial 4/1
R2(config)#ip route 3.0.0.0 255.0.0.0 serial 4/1
R2(config)#ip route 4.0.0.0 255.0.0.0 serial 4/2
R2(config)#ip route 40.0.0.0 255.0.0.0 serial 4/2
R2(config)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 serial 4/1
R3(config)#exit
R4(config)#ip route 0.0.0.0 0.0.0.0 serial 4/2
R4(config)#exit
R1#show ip route static
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
S* 0.0.0.0/0 is directly connected, Serial4/0
R2#show ip route static
Gateway of last resort is not set
S 10.0.0.0/8 is directly connected,
Serial4/0
S 30.0.0.0/8 is directly connected,
Serial4/1
S 40.0.0.0/8 is directly connected,
Serial4/2
R3#show ip route static
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
S* 0.0.0.0/0 is directly connected, Serial4/1
R4#show ip route static
Gateway of last resort is 0.0.0.0 to network 0.0.0.0
S* 0.0.0.0/0 is directly connected, Serial4/2
R1(config)#interface tunnel 1023
R1(config-if)#ip address 192.168.10.1 255.255.255.0
R1(config-if)#tunnel source 1.1.1.1
R1(config-if)#tunnel mode gre multipoint
R1(config-if)#IP NHRP network-id 1
R1(config-if)#IP NHRP map 192.168.10.2 3.3.3.2
R1(config-if)#IP NHRP map 192.168.10.3 4.4.4.2
R1(config-if)#exit
R3(config)#interface tunnel 1023
R3(config-if)#ip address 192.168.10.2 255.255.255.0
R3(config-if)#tunnel source 3.3.3.2
R3(config-if)#tunnel mode gre multipoint
R3(config-if)#IP NHRP network-id 3
R3(config-if)#IP NHRP map 192.168.10.1 1.1.1.1
R3(config-if)#IP NHRP map 192.168.10.3 4.4.4.2
R3(config-if)#exit
R4(config)#interface tunnel 1023
R4(config-if)#ip address 192.168.10.3 255.255.255.0
R4(config-if)#tunnel source 4.4.4.2
R4(config-if)#tunnel mode gre multipoint
R4(config-if)#IP NHRP network-id 3
R4(config-if)#IP NHRP map 192.168.10.1 1.1.1.1
R4(config-if)#IP NHRP map 192.168.10.2 3.3.3.2
R4(config-if)#exit
R1#show ip interface brief tunnel 1023
Interface IP-Address OK? Method Status Protocol
Tunnel1023 192.168.10.1 YES manual up up
R1#show ip nhrp
192.168.10.2/32 via 192.168.10.2
Tunnel1023 created 00:40:57, never expire
Type: static, Flags: used
NBMA address: 3.3.3.2
192.168.10.3/32 via 192.168.10.3
Tunnel1023 created 00:40:38, never expire
Type: static, Flags:
NBMA address: 4.4.4.2
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel1023, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 3.3.3.2 192.168.10.2 NHRP never S
1 4.4.4.2 192.168.10.3 NHRP never S
R3#show ip interface brief tunnel 1023
Interface IP-Address OK? Method Status Protocol
Tunnel1023 192.168.10.2 YES manual up up
R3#show ip nhrp
192.168.10.1/32 via 192.168.10.1
Tunnel1023 created 00:39:56, never expire
Type: static, Flags: used
NBMA address: 1.1.1.1
192.168.10.3/32 via 192.168.10.3
Tunnel1023 created 00:39:25, never expire
Type: static, Flags: used
NBMA address: 4.4.4.2
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel1023, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.1.1 192.168.10.1 NHRP never S
1 4.4.4.2 192.168.10.3 NHRP never S
R4#show ip interface brief tunnel 1023
Interface IP-Address OK? Method Status Protocol
Tunnel1023 192.168.10.3 YES manual up up
R4#show ip nhrp
192.168.10.1/32 via 192.168.10.1
Tunnel1023 created 00:36:25, never expire
Type: static, Flags: used
NBMA address: 1.1.1.1
192.168.10.2/32 via 192.168.10.2
Tunnel1023 created 00:36:16, never expire
Type: static, Flags: used
NBMA address: 3.3.3.2
R4#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel1023, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.1.1 192.168.10.1 NHRP never S
1 3.3.3.2 192.168.10.2 NHRP never S
( let see spokes router can get each other or not without using a hub)
R1#ping 192.168.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/71/256 ms
R1#ping 192.168.10.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/43/116 ms
R1#traceroute 30.1.1.1
Type escape sequence to abort.
Tracing the route to 30.1.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 1.1.1.2 236 msec 28 msec 16 msec
2 3.3.3.2 112 msec 16 msec 16 msec
R1#traceroute 192.168.10.2
Type escape sequence to abort.
Tracing the route to 192.168.10.2
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.2 32 msec 28 msec 28 msec
R1#traceroute 192.168.10.3
Type escape sequence to abort.
Tracing the route to 192.168.10.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.3 20 msec 40 msec 36 msec
R3#ping 192.168.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/83/100 ms
R3#ping 192.168.10.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/27/32 ms
R3#traceroute 40.1.1.1
Type escape sequence to abort.
Tracing the route to 40.1.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 3.3.3.1 64 msec 24 msec 8 msec
2 4.4.4.2 12 msec 28 msec 16 msec
R3#traceroute 192.168.10.1
Type escape sequence to abort.
Tracing the route to 192.168.10.1
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.1 64 msec 20 msec 28 msec
( here is the screenshot of the previous lab DMVPN PHASE 1)
R3#traceroute 192.168.10.3
Type escape sequence to abort.
Tracing the route to 192.168.10.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.3 12 msec 52 msec 44 msec
R3#traceroute 40.1.1.1
Type escape sequence to abort.
Tracing the route to 40.1.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 3.3.3.1 4 msec 28 msec 20 msec
2 4.4.4.2 8 msec 32 msec 16 msec
R4#ping 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/40/84 ms
R4#ping 192.168.10.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/27/32 ms
R4#ping 192.168.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/29/48 ms
R4#traceroute 192.168.10.1
Type escape sequence to abort.
Tracing the route to 192.168.10.1
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.1 60 msec 40 msec 24 msec
R4#traceroute 192.168.10.2
Type escape sequence to abort.
Tracing the route to 192.168.10.2
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.10.2 12 msec 48 msec 44 msec
R4#traceroute 10.1.1.1
Type escape sequence to abort.
Tracing the route to 10.1.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 4.4.4.1 16 msec 16 msec 8 msec
2 1.1.1.1 16 msec 32 msec 20 msec
(Let's see how to configure dynamic mappings )
We are modifying our previous static lab into dynamic. we are going to reconfigure our tunnel 1023 and DMVPN.
R1(config)# NO INTERFACE TUNNEL 1023
R1(config)#interface tunnel 400
R1(config-if)#ip address 192.168.100.1 255.255.255.0
R1(config-if)#tunnel source 1.1.1.1
R1(config-if)#tunnel mode gre multipoint
R1(config-if)#ip nhrp network-id 10
R1(config-if)#exit
R3(config)#NO INTERFACE TUNNEL 1023
R3(config)#interface tunnel 400
R3(config-if)#ip address 192.168.100.2 255.255.255.0
R3(config-if)#tunnel source 3.3.3.2
R3(config-if)#tunnel mode gre multipoint
R3(config-if)#ip nhrp network-id 20
R3(config-if)#ip nhrp map 192.168.100.1 1.1.1.1
R3(config-if)#ip nhrp nhs 192.168.100.1
R3(config-if)#exit
R4(config)#NO INTERFACE TUNNEL 1023
R4(config)#interface tunnel 400
R4(config-if)#ip address 192.168.100.3 255.255.255.0
R4(config-if)#tunnel source 4.4.4.2
R4(config-if)#tunnel mode gre multipoint
R4(config-if)#ip nhrp network-id 30
R4(config-if)# ip nhrp map 192.168.100.1 1.1.1.1
R4(config-if)#ip nhrp nhs 192.168.100.1
R4(config-if)#exit
R1#show ip nhrp
192.168.100.2/32 via 192.168.100.2
Tunnel400 created 00:05:28, expire 01:54:31
Type: dynamic, Flags: unique registered used
NBMA address: 3.3.3.2
192.168.100.3/32 via 192.168.100.3
Tunnel400 created 00:01:14, expire 01:58:45
Type: dynamic, Flags: unique registered used
NBMA address: 4.4.4.2
R1#show DMVPN
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel400, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 3.3.3.2 192.168.100.2 UP 00:17:10 D
1 4.4.4.2 192.168.100.3 UP 00:12:56 D
R1#traceroute 192.168.100.2
Type escape sequence to abort.
Tracing the route to 192.168.100.2
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.2 48 msec 48 msec 24 msec
R1#traceroute 192.168.100.3
Type escape sequence to abort.
Tracing the route to 192.168.100.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.3 72 msec 28 msec 40 msec
R3#show ip nhrp
192.168.100.1/32 via 192.168.100.1
Tunnel400 created 00:06:05, never expire
Type: static, Flags: used
NBMA address: 1.1.1.1
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel400, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.1.1 192.168.100.1 UP 00:06:15 S
R3#traceroute 192.168.100.1
Type escape sequence to abort.
Tracing the route to 192.168.100.1
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.1 80 msec 36 msec 32 msec
R3#traceroute 192.168.100.3
Type escape sequence to abort.
Tracing the route to 192.168.100.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.1 80 msec 52 msec 16 msec
2 192.168.100.3 120 msec 20 msec 40 msec
R3#traceroute 192.168.100.3
Type escape sequence to abort.
Tracing the route to 192.168.100.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.3 64 msec 88 msec 28 msec
R3#traceroute 192.168.100.3
Type escape sequence to abort.
Tracing the route to 192.168.100.3
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.3 28 msec 16 msec 40 msec
R4#show ip nhrp
192.168.100.1/32 via 192.168.100.1
Tunnel400 created 00:01:37, never expire
Type: static, Flags: used
NBMA address: 1.1.1.1
R4#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel400, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 1.1.1.1 192.168.100.1 UP 00:02:08 S
R4#traceroute 192.168.100.1
Type escape sequence to abort.
Tracing the route to 192.168.100.1
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.1 24 msec 48 msec 44 msec
R4#traceroute 192.168.100.2
Type escape sequence to abort.
Tracing the route to 192.168.100.2
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.100.2 28 msec 32 msec 36 msec