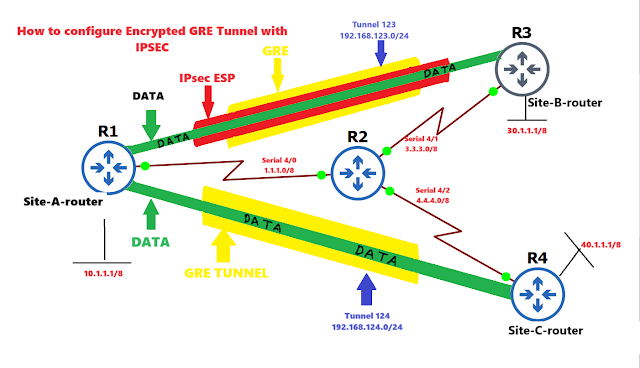
DMVPN (Dynamic Multipoint VPN) is a routing technology introduced by Cisco that allows you to build a VPN network with multiple sites without having to statically configure all devices. It uses a "hub and spoke" network topology, where the spokes can communicate directly without going through the hub. DMVPN supports encryption through IPsec, which makes it a popular choice for connecting different sites using regular Internet connections. It's a great backup or alternative to private networks like MPLS VPN. In other words, DMVPN combines mGRE + NHRP + DRP (dynamic routing protocol) and IPsec.
let's take a look at all the technologies: -
Multipoint GRE (mGRE)
Our regular GRE tunnels are point-to-point and don’t scale well. It becomes messy quickly so many point-to-point tunnels. but When we use GRE Multipoint, there will be only one tunnel interface on each router. mGRE interfaces do not have a tunnel destination. It keeps costs low, minimizing configuration complexity, and increasing flexibility. Multipoint GRE(Mgre) Uses tunnel source and tunnel mode (mgre). The tunnel can have many endpoints by using a single tunnel interface. The endpoint can be configured as GRE or MGRE and Mapping is done by NHRP Protocol.
https://mpls.internetworks.in/2021/02/what-is-network-tunneling-and-how-to.html
NHRP (Next Hop Resolution Protocol)
We want something that can help our router figure out what the public IP address is of the other router, we do this with the help of a protocol called NHRP (Next Hop Resolution Protocol). Next hop resolution protocol (NHRP) Maps the tunnel IP with NBMA address (public IP ) (static or dynamic). NHRP Provides layer 2 address resolution protocol and caching services similar to ARP and inverse ARP. It only builds a dynamic database stored on the hub with information about spokes IP addresses.
https://mpls.internetworks.in/2021/02/what-is-dmvpn-dynamic-multipoint-vpn.html
Dynamic routing protocol
Dynamic routing is used to find networks and update routing tables on routers dynamically. It is easier than using static or default routing, but it will cost you in terms of router CPU processing and bandwidth on network links.
https://www.internetworks.in/2018/10/open-shortest-path-first-ospf-basic.html
https://www.internetworks.in/2018/10/eigrp-basic.html
IPsec encryption
(Internet Protocol Security) IPSec is a set of protocols developed by the Internet Engineering Task Force (IETF). Internet protocol security (IPsec) is a framework that helps us to protect our IP traffic on the network layer. Why? Because the ( internet protocol) IP protocol itself doesn’t have any security features at all. IPsec allows two or more hosts to communicate securely by authenticating and encrypting each IP packet of a communication session.
https://mpls.internetworks.in/2021/07/what-is-ipsec-internet-protocol.html
DMVPN has different three versions. we call phases.
Phase 3 In phase 3 we configure the (IP NHRP Redirect) command on the hub router and the IP NHRP shortcut command on the spokes routers.
Let's see the configuration:-
Topology:-
- Configure the topology as per the diagram
- Configure the IP addresses as per the topology
- Configure static and default route
- Configure the tunnel 192.168.1.0/24
- Configure EIGRP 1 and advertise tunnel interface and LAN
- Configure NHRP Redirect on the HUB
- Configure NHRP Shortcut on the spokes
- verify with show commands and trace commands.
R1(config)#hostname Site-A-R-
Site-A-R-(config)#interface serial 4/1
Site-A-R-(config-if)#ip address 1.1.1.1 255.0.0.0
Site-A-R-(config-if)#no shutdown
Site-A-R-(config-if)#exit
Site-A-R-(config)#interface fastethernet 0/0
Site-A-R-(config-if)#ip address 10.1.1.1 255.0.0.0
Site-A-R-(config-if)#no shutdown
Site-A-R-(config-if)#no keepalive
Site-A-R-(config-if)#exit
Site-A-R-(config)#end
Site-A-R-#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.1.1 YES manual up up
Serial4/1 1.1.1.1 YES manual up up
Site-A-R-# wr
Building configuration...
[OK]
R2(config)#hostname Site-B-R-
Site-B-R-(config)#interface serial 4/2
Site-B-R-(config-if)#ip address 2.2.2.1 255.0.0.0
Site-B-R-(config-if)#no shutdown
Site-B-R-(config-if)#exit
Site-B-R-(config)#interface fastEthernet 0/0
Site-B-R-(config-if)#ip address 20.1.1.1 255.0.0.0
Site-B-R-(config-if)#no shutdown
Site-B-R-(config-if)#no keepalive
Site-B-R-(config-if)#exit
Site-B-R-(config)#end
Site-B-R-#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 20.1.1.1 YES manual up up
Serial4/2 2.2.2.1 YES manual up up
Site-B-R-#wr
Building configuration...
[OK]
Site-C-R-(config)#interface serial 4/3
Site-C-R-(config-if)#ip address 3.3.3.1 255.0.0.0
Site-C-R-(config-if)#no shutdown
Site-C-R-(config-if)#exit
Site-C-R-(config)#interface fastethernet 0/0
Site-C-R-(config-if)#ip address 30.1.1.1 255.0.0.0
Site-C-R-(config-if)#no keepalive
Site-C-R-(config-if)#no shutdown
Site-C-R-(config-if)#exit
Site-C-R-(config)#end
Site-C-R-#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 30.1.1.1 YES manual up up
Serial4/3 3.3.3.1 YES manual up up
Site-C-R-# wr
Building configuration...
[OK]
R4(config)#hostname Site-D-R-
Site-D-R-(config)#interface serial 4/4
Site-D-R-(config-if)#ip address 4.4.4.1 255.0.0.0
Site-D-R-(config-if)#no shutdown
Site-D-R-(config-if)#exit
Site-D-R-(config)#interface fastEthernet 0/0
Site-D-R-(config-if)#ip address 40.1.1.1 255.0.0.0
Site-D-R-(config-if)#no shutdown
Site-D-R-(config-if)#exit
Site-D-R-#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 40.1.1.1 YES manual up up
Serial4/4 4.4.4.1 YES manual up up
Site-D-R-#wr
Building configuration...
[OK]
R5(config)#hostname INTERNET-ROUTER-
INTERNET-ROUTER-(config)#interface serial 4/1
INTERNET-ROUTER-(config-if)#ip address 1.1.1.2 255.0.0.0
INTERNET-ROUTER-(config-if)#no shutdown
INTERNET-ROUTER-(config-if)#exit
INTERNET-ROUTER-(config)#interface serial 4/2
INTERNET-ROUTER-(config-if)#ip address 2.2.2.2 255.0.0.0
INTERNET-ROUTER-(config-if)#no shutdown
INTERNET-ROUTER-(config-if)#exit
INTERNET-ROUTER-(config)#interface serial 4/3
INTERNET-ROUTER-(config-if)#ip address 3.3.3.2 255.0.0.0
INTERNET-ROUTER-(config-if)#no shutdown
INTERNET-ROUTER-(config-if)#exit
INTERNET-ROUTER-(config)#interface serial 4/4
INTERNET-ROUTER-(config-if)#ip address 4.4.4.2 255.0.0.0
INTERNET-ROUTER-(config-if)#no shutdown
INTERNET-ROUTER-(config-if)#exit
INTERNET-ROUTER-#show ip interface brief
Interface IP-Address OK? Method Status Protocol
Serial4/1 1.1.1.2 YES manual up up
Serial4/2 2.2.2.2 YES manual up up
Serial4/3 3.3.3.2 YES manual up up
Serial4/4 4.4.4.2 YES manual up up
INTERNET-ROUTER-#wr
Building configuration...
[OK]
Site-A-R-(config)#ip route 0.0.0.0 0.0.0.0 serial 4/1
Site-A-R-(config)#end
Site-A-R-#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/1
Site-A-R-#wr
Building configuration...
[OK]
Site-B-R-(config)#ip route 0.0.0.0 0.0.0.0 serial 4/2
Site-B-R-(config)#end
Site-B-R-#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/2
Site-B-R-#write
Building configuration...
[OK]
Site-C-R-(config)#ip route 0.0.0.0 0.0.0.0 serial 4/3
Site-C-R-(config)#end
Site-C-R-#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/3
Site-C-R-#write
Building configuration...
[OK]
Site-D-R-(config)#ip route 0.0.0.0 0.0.0.0 serial 4/4
Site-D-R-(config)#end
Site-D-R-#show ip route static
S* 0.0.0.0/0 is directly connected, Serial4/4
Site-D-R-#write
Building configuration...
[OK
Site-A-R-(config)#interface tunnel 1
Site-A-R-(config-if)#ip address 192.168.1.1 255.255.255.0
Site-A-R-(config-if)#tunnel source 1.1.1.1
Site-A-R-(config-if)#tunnel mode gre multipoint
Site-A-R-(config-if)#ip nhrp network-id 1
Site-A-R-(config-if)#ip nhrp map multicast dynamic
Site-A-R-(config-if)#exit
Site-A-R-#show interfaces tunnel 1
Tunnel1 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.1/24
MTU 17916 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 1.1.1.1
Tunnel protocol/transport multi-GRE/IP
Site-A-R-(config)#router eigrp 1
Site-A-R-(config-router)#network 192.168.1.0
Site-A-R-(config-router)#network 10.0.0.0
Site-A-R-(config-router)#no au
Site-A-R-(config-router)#no auto-summary
Site-A-R-(config-router)#exit
Site-A-R-(config)#interface tunnel 1
Site-A-R-(config-if)#no ip split-horizon eigrp 1
Site-A-R-(config-if)#ip next-hop-self eigrp 1
Site-A-R-(config-if)#ip nhrp redirect
Site-A-R-(config-if)#exit
Site-A-R-(config)#end
Site-B-R-(config)#interface tunnel 1
Site-B-R-(config-if)#ip address 192.168.1.2 255.255.255.0
Site-B-R-(config-if)#tunnel source 2.2.2.1
Site-B-R-(config-if)#tunnel mode gre multipoint
Site-B-R-(config-if)#ip nhrp network-id 2
Site-B-R-(config-if)#ip nhrp map 192.168.1.1 1.1.1.1
Site-B-R-(config-if)#ip nhrp nhs 192.168.1.1
Site-B-R-(config-if)#ip nhrp map multicast 1.1.1.1
Site-B-R-(config-if)#exit
Site-B-R-#show interfaces tunnel 1
Tunnel1 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.2/24
MTU 17916 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 2.2.2.1
Tunnel protocol/transport multi-GRE/IP
Site-B-R-(config)#router eigrp 1
Site-B-R-(config-router)#network 192.168.1.0
Site-B-R-(config-router)#network 20.0.0.0
Site-B-R-(config-router)#no auto-summary
Site-B-R-(config-router)#exit
Site-B-R-(config)#interface tunnel 1
Site-B-R-(config-if)#ip nhrp shortcut
Site-B-R-(config-if)#exit
Site-B-R-(config)#end

Site-B-R-#traceroute 10.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 10.1.1.1
1 192.168.1.1 56 msec 56 msec 60 msec
Site-C-R-(config)#interface tunnel 1
Site-C-R-(config-if)#ip address 192.168.1.3 255.255.255.0
Site-C-R-(config-if)#tunnel source 3.3.3.1
Site-C-R-(config-if)#tunnel mode gre multipoint
Site-C-R-(config-if)#ip nhrp network-id 3
Site-C-R-(config-if)#ip nhrp map 192.168.1.1 1.1.1.1
Site-C-R-(config-if)#ip nhrp nhs 192.168.1.1
Site-C-R-(config-if)#ip nhrp map multicast 1.1.1.1
Site-C-R-(config-if)#exit
Site-C-R-#show interfaces tunnel 1
Tunnel1 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.3/24
MTU 17916 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 3.3.3.1
Tunnel protocol/transport multi-GRE/IP
Site-C-R-(config)#router eigrp 1
Site-C-R-(config-router)#network 192.168.1.0
Site-C-R-(config-router)#network 30.0.0.0
Site-C-R-(config-router)#no auto-summary
Site-C-R-(config-router)#exit
Site-C-R-(config)#interface tunnel 1
Site-C-R-(config-if)#ip nhrp shortcut
Site-C-R-(config-if)#exit
Site-C-R-(config)#end

Site-C-R-#traceroute 10.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 10.1.1.1
1 192.168.1.1 64 msec 64 msec 60 msec
Site-C-R-#traceroute 20.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 20.1.1.1
1 192.168.1.2 56 msec 64 msec 60 msec
Site-D-R-(config)#interface tunnel 1
Site-D-R-(config-if)#ip address 192.168.1.4 255.255.255.0
Site-D-R-(config-if)#tunnel source 4.4.4.1
Site-D-R-(config-if)#tunnel mode gre multipoint
Site-D-R-(config-if)#ip nhrp network-id 4
Site-D-R-(config-if)#ip nhrp map 192.168.1.1 1.1.1.1
Site-D-R-(config-if)#ip nhrp nhs 192.168.1.1
Site-D-R-(config-if)#ip nhrp map multicast 1.1.1.1
Site-D-R-(config-if)#exit
Site-D-R-#show interfaces tunnel 1
Tunnel1 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.4/24
MTU 17916 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 4.4.4.1
Tunnel protocol/transport multi-GRE/IP
Site-D-R-(config)#router eigrp 1
Site-D-R-(config-router)#network 192.168.1.0
Site-D-R-(config-router)#network 40.0.0.0
Site-D-R-(config-router)#exit
Site-D-R-(config)#interface tunnel 1
Site-D-R-(config-if)#ip nhrp shortcut
Site-D-R-(config-if)#exit
Site-D-R-(config)#end

Site-D-R-#traceroute 10.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 10.1.1.1
1 192.168.1.1 56 msec 52 msec 72 msec
Site-D-R-#traceroute 20.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 20.1.1.1
1 192.168.1.1 56 msec 64 msec 56 msec
2 192.168.1.2 128 msec 116 msec 100 msec
Site-D-R-#traceroute 30.1.1.1 source fastEthernet 0/0
Type escape sequence to abort.
Tracing the route to 30.1.1.1
1 192.168.1.1 56 msec 60 msec 72 msec
2 192.168.1.3 128 msec 144 msec92 msec