In this previous session, we discussed MPLS, DMVPN basic to advance, and IPSec. I am assuming you are familiar with these topics. in this section are going to configure IPsec Over DMVPN.
1. Introduction of MPLS
2.What is MPLS Label distributing protocol (LDP) ? How LDP works?
3.how to configure MPLS LDP Peering ?
4.What is MPLS L3 VPN ? How to configure?
5.How to configure MPLS L3 VPN with RIPv2 ?
6.How to configure MPLS L3 VPN with EIGRP ?
7.How to configure MPLS L3 VPN with OSPF ?
8.What is OSPF Sham Links? how to configure OSPF Sham Links?
let's see the configuration:-
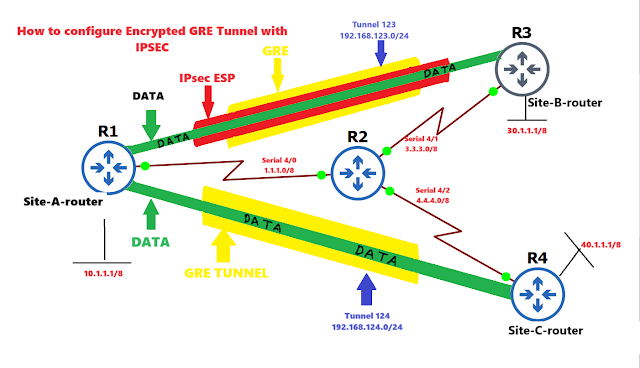
Topology:-
R1(config)#interface serial 4/0
R1(config-if)#ip address 12.1.1.1 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#exit
R1(config)#interface fastEthernet 0/0
R1(config-if)#ip address 10.1.1.1 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#exit
R2(config)#interface serial 4/0
R2(config-if)#ip address 12.1.1.2 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface serial 4/1
R2(config-if)#ip address 23.1.1.1 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface fastEthernet 0/0
R2(config-if)#ip address 20.1.1.1 255.255.255.0
R2(config-if)#no keepalive
R2(config-if)#exit
R2(config)#interface serial 4/2
R2(config-if)#ip address 24.1.1.1 255.255.255.0
R2(config-if)#no shutdown
R2(config-if)#exit
R2(config)#interface serial 4/1
R2(config-if)#ip address 23.1.1.1 255.255.255.0
R2(config-if)#no shutdown
R3(config)#interface serial 4/1
R3(config-if)#ip address 23.1.1.2 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#exit
R3(config)#interface loopback 0
R3(config-if)#ip address 192.168.30.1 255.255.255.0
R3(config-if)#exit
R3(config)#interface fastEthernet 0/0
R3(config-if)#ip address 30.1.1.1 255.255.255.0
R3(config-if)#no shutdown
R3(config-if)#no keepalive
R3(config-if)#exit
R4(config)#interface serial 4/2
R4(config-if)#ip address 24.1.1.2 255.255.255.0
R4(config-if)#no shutdown
R4(config-if)#exit
R4(config)#interface fastEthernet 0/0
R4(config-if)#ip address 40.1.1.1 255.255.255.0
R4(config-if)#no shutdown
R4(config-if)#no keepalive
R4(config-if)#exit
R4(config)#interface loopback 0
R4(config-if)#ip address 192.168.30.1 255.255.255.0
R4(config-if)#no shutdown
R4(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 12.1.1.2
R1(config)#exit
R2(config)#ip route 192.168.10.0 255.255.255.0 12.1.1.1.
R2(config)#ip route 10.1.1.0 255.255.255.0 12.1.1.1
R2(config)#ip route 192.168.30.0 255.255.255.0 23.1.1.2
R2(config)#ip route 30.1.1.0 255.255.255.0 23.1.1.2
R2(config)#ip route 40.1.1.0 255.255.255.0 24.1.1.2
R2(config)#ip route 192.168.40.0 255.255.255.0 24.1.1.2
R2(config)#ip route 24.1.1.0 255.255.255.0 24.1.1.2
R2(config)#ip route 23.1.1.0 255.255.255.0 2.1.1.2
R2(config)#ip route 23.1.1.0 255.255.255.0 23.1.1.2
R2(config)#ip route 12.1.1.0 255.255.255.0 12.1.1.1
R2(config)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 23.1.1.1
R3(config)#exit
R4(config)#ip route 0.0.0.0 0.0.0.0 24.1.1.1
R4(config)#exit
R1(config)#interface tunnel 4321
R1(config-if)#ip address 192.168.1.1 255.255.255.0
R1(config-if)#tunnel source 12.1.1.1
R1(config-if)#tunnel mode gre multipoint
*Oct 23 15:53:38.431: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel4321, changed state to up
R1(config-if)#ip nhrp network-id 1
R1(config-if)#exit
R3(config)#interface tunnel 4321
*Oct 23 15:53:52.263: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel4321, changed state to down
R3(config-if)#ip address 192.168.1.3 255.255.255.0
R3(config-if)#tunnel source 23.1.1.2
R3(config-if)#tunnel destination 12.1.1.1
*Oct 23 15:54:23.315: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel4321, changed state to up
R3(config-if)#ip nhrp network-id 2
R3(config-if)#ip nhrp nhs 192.168.1.1
R3(config-if)#ip nhrp map 192.168.1.1 12.1.1.1
R3(config-if)#exit
R4(config)#interface tunnel 4321
*Oct 23 15:55:05.111: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel4321, changed state to down
R4(config-if)#ip address 192.168.1.4 255.255.255.0
R4(config-if)#tunnel source 24.1.1.2
R4(config-if)#tunnel destination 12.1.1.1
*Oct 23 15:55:40.667: %LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel4321, changed state to up
R4(config-if)#ip nhrp network-id 3
R4(config-if)#ip nhrp nhs 192.168.1.1
R4(config-if)#ip nhrp map 192.168.1.1 12.1.1.1
R4(config-if)#exit
R1(config)#interface tunnel 4321
R1(config-if)#ip nhrp map multicast dynamic
R1(config-if)#exit
R1(config)#router ospf 1
R1(config-router)#router-id 1.1.1.1
R1(config-router)#network 10.0.0.0 255.0.0.0 area 0
R1(config-router)#network 192.168.1.0 255.0.0.0 area 0
R1(config-router)#exit
R3(config)#router ospf 1
R3(config-router)#router-id 3.3.3.3
R3(config-router)#network 30.0.0.0 255.0.0.0 area 0
R3(config-router)#network 192.168.1.0 255.0.0.0 area 0
R3(config-router)#exit
R3(config)#interface tunnel 4321
R3(config-if)#ip ospf network point-to-mult
R3(config-if)#ip ospf network point-to-multipoint
R3(config-if)#exit
R4(config)#router ospf 1
R4(config-router)#router-id 4.4.4.4
R4(config-router)#network 40.0.0.0 255.0.0.0 area 0
R4(config-router)#network 192.168.1.0 255.0.0.0 area 0
R4(config-router)#exit
R4(config)#interface tunnel 4321
R4(config-if)#ip ospf network point-to-mul
R4(config-if)#ip ospf network point-to-multipoint
R4(config-if)#exit
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#encryption aes
R1(config-isakmp)#hash sha
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 5
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 0 mpls123 address 0.0.0.0
R3(config)#crypto isakmp policy 10
R3(config-isakmp)#encryption aes
R3(config-isakmp)#hash sha
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#group 5
R3(config-isakmp)#exit
R1(config)#crypto isakmp key 0 mpls123 address 0.0.0.0
R4(config)#crypto isakmp policy 10
R4(config-isakmp)#encryption aes
R4(config-isakmp)#hash sha
R4(config-isakmp)#authentication pre-share
R4(config-isakmp)#group 5
R4(config-isakmp)#exit
{You can configure more specific IP address of the peers but we are using address 0.0.0.0}
R1(config)#crypto isakmp key 0 mpls123 address 23.1.1.2
R1(config)#crypto isakmp key 0 mpls123 address 24.1.1.2
R3(config)#crypto isakmp key 0 mpls123 address 12.1.1.1
R3(config)#crypto isakmp key 0 mpls123 address 24.1.1.2
R4(config)#crypto isakmp key 0 mpls123 address 12.1.1.1
R4(config)#crypto isakmp key 0 mpls123 address 23.1.1.2
R1(config)#crypto isakmp key 0 mpls123 address 0.0.0.0
R1#
*Oct 23 16:08:14.239: %OSPF-5-ADJCHG: Process 1, Nbr 4.4.4.4 on Tunnel4321 from LOADING to FULL, Loading Done
R1#
*Oct 23 16:08:23.587: %OSPF-5-ADJCHG: Process 1, Nbr 3.3.3.3 on Tunnel4321 from LOADING to FULL, Loading Don
R1(config)#crypto ipsec transform-set MYSET esp-3des esp-md5-hmac
R1(cfg-crypto-trans)#exit
R3(config)#crypto ipsec transform-set MYSET esp-3des esp-md5-hmac
R3(cfg-crypto-trans)#exit
R4(config)#crypto ipsec transform-set MYSET esp-3des esp-md5-hmac
R4(cfg-crypto-trans)#exit
R1(config)#crypto IPsec profile INTERNETWORKS
R1(ipsec-profile)#set transform-set MYSET
R1(ipsec-profile)#exit
R1(config)#interface tunnel 4321
R1(config-if)#tunnel protection IPsec profile INTERNETWORKS
R1(config-if)#EXIT
*Oct 23 16:12:45.259: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R3(config)#crypto IPsec profile INTERNETWORKS
R3(ipsec-profile)#set transform-set MYSET
R3(ipsec-profile)#exit
R3(config)#interface tunnel 4321
R3(config-if)#tunnel protection IPsec profile INTERNETWORKS
R3(config-if)#EXIT
*Oct 23 16:12:45.259: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R4(config)#crypto IPsec profile INTERNETWORKS
R4(ipsec-profile)#set transform-set MYSET
R4(ipsec-profile)#exit
R4(config)#interface tunnel 4321
R4(config-if)#tunnel protection IPsec profile INTERNETWORKS
R4(config-if)#EXIT
*Oct 23 16:12:45.259: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1#show crypto session
Crypto session current status
Interface: Tunnel4321
Session status: UP-ACTIVE
Peer: 24.1.1.2 port 500
IKEv1 SA: local 12.1.1.1/500 remote 24.1.1.2/500 Active
IPSEC FLOW: permit 47 host 12.1.1.1 host 24.1.1.2
Active SAs: 4, origin: crypto map
Interface: Tunnel4321
Session status: UP-ACTIVE
Peer: 23.1.1.2 port 500
IKEv1 SA: local 12.1.1.1/500 remote 23.1.1.2/500 Active
IPSEC FLOW: permit 47 host 12.1.1.1 host 23.1.1.2
Active SAs: 4, origin: crypto map
R3#show crypto session
Crypto session current status
Interface: Tunnel4321
Session status: UP-ACTIVE
Peer: 12.1.1.1 port 500
IKEv1 SA: local 23.1.1.2/500 remote 12.1.1.1/500 Active
IPSEC FLOW: permit 47 host 23.1.1.2 host 12.1.1.1
Active SAs: 4, origin: crypto map
R4#show crypto session
Crypto session current status
Interface: Tunnel4321
Session status: UP-ACTIVE
Peer: 12.1.1.1 port 500
IKEv1 SA: local 24.1.1.2/500 remote 12.1.1.1/500 Active
IPSEC FLOW: permit 47 host 24.1.1.2 host 12.1.1.1
Active SAs: 4, origin: crypto map
R1#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel4321, IPv4 NHRP Details
Type:Hub, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 23.1.1.2 192.168.1.3 UP 01:34:52 D
1 24.1.1.2 192.168.1.4 UP 01:33:09 D
R3#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel4321, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 12.1.1.1 192.168.1.1 UP 00:46:35 S
R4#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel4321, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 12.1.1.1 192.168.1.1 UP 00:46:45 S
R1#show crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set MYSET: { esp-3des esp-md5-hmac }
will negotiate = { Tunnel, },
R3#show crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set MYSET: { esp-3des esp-md5-hmac }
will negotiate = { Tunnel, },
R4#show crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set MYSET: { esp-3des esp-md5-hmac }
will negotiate = { Tunnel, },
R1#ping 192.168.1.3 source 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 56/65/88 ms
R1#ping 192.168.1.4 source 10.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.4, timeout is 2 seconds:
Packet sent with a source address of 10.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 56/69/112 ms
R4#ping 192.168.1.1 source 40.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
Packet sent with a source address of 40.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 56/67/92 ms
R4#ping 192.168.1.3 source 40.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
Packet sent with a source address of 40.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 68/79/84 ms
R1#show crypto ipsec profile
IPSEC profile INTERNETWORKS
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
MYSET: { esp-3des esp-md5-hmac } ,
}
IPSEC profile default
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
default: { esp-aes esp-sha-hmac } ,
}
R3#show crypto ipsec profile
IPSEC profile INTERNETWORKS
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
MYSET: { esp-3des esp-md5-hmac } ,
}
IPSEC profile default
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
default: { esp-aes esp-sha-hmac } ,
}
R4#show crypto IPsec profile
IPSEC profile INTERNETWORKS
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
MYSET: { esp-3des esp-md5-hmac } ,
}
IPSEC profile default
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
default: { esp-aes esp-sha-hmac } ,
}




.png)



















